Cyber Security
Protecting your business data, identity and reputation from cyber-attacks has never been more important than it is today. Outbound Solutions forward-thinking, thorough approach to cyber security is backed by unmatched technical expertise and hands-on experience. Clients rely on our cyber security and SOC team to resolve data breaches, restore data, and create new solutions to prevent future threats.
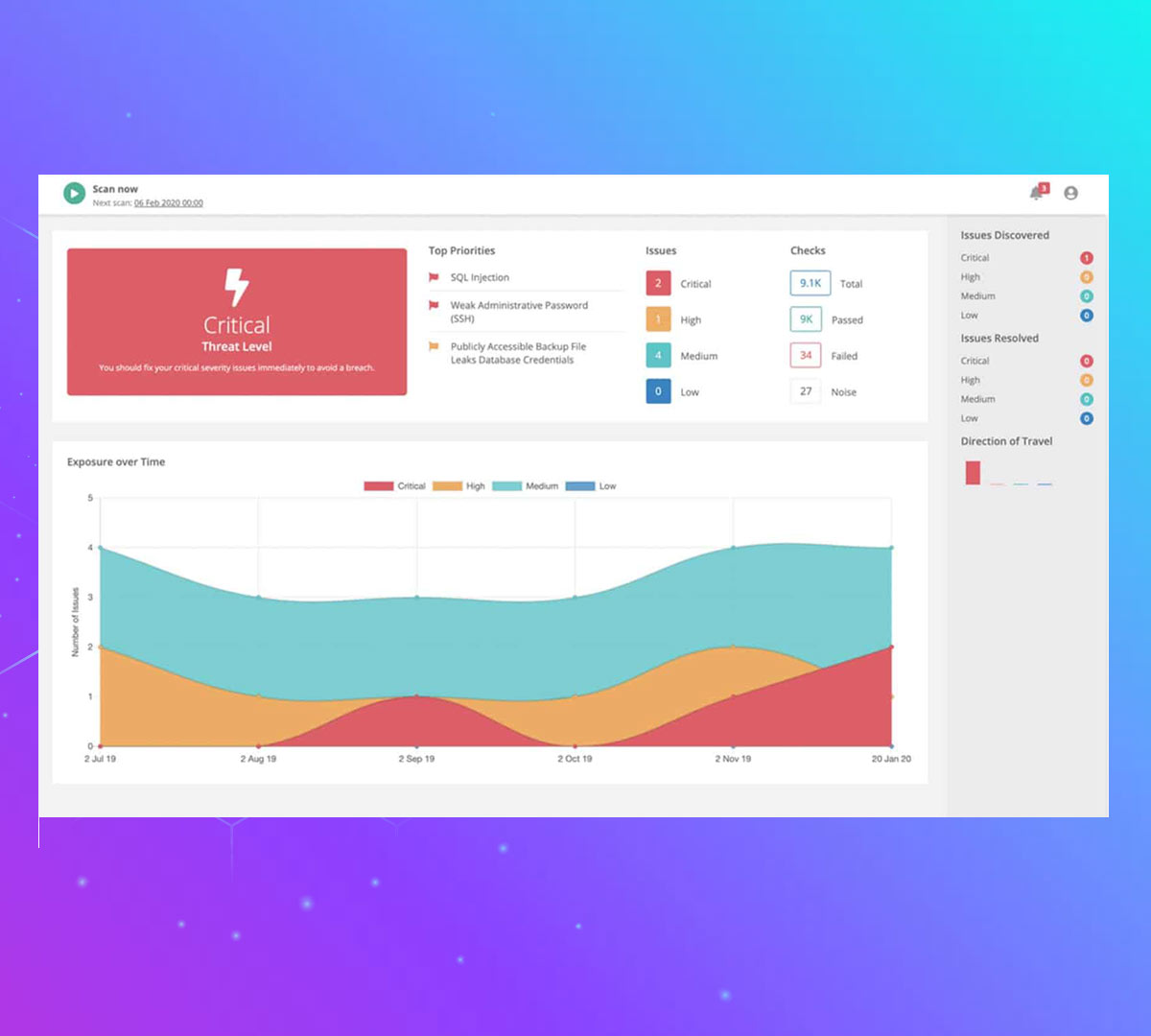
Cyber Security Experts you can trust
We have dedicated engineers with more than 20 years of experience in IT security. Our clients benefit greatly from having access to multiple Cyber Security experts with different specialisations. In most cases, it is impossible to identify a single resource with the relevant training and experience in all fields and with knowledge of all types of cyber threats.
Chief Information Security Officer’s (CISO), Security Engineers, Security Consultants and qualified Security Auditors can be expensive for even the multi-national companies. Having access to our consultants not only brings this price point down to a manageable monthly cost, allows customers to have access to range of comprehensive and advanced IT Security solutions that are managed regularly or on an ad hoc basis.
Outbound Solutions Cyber Security Services
Cyber Security Architecture and Strategy
Security begins with strategy and relies on infrastructure. Our experts design top-of-the-line network and architecture security solutions to protect your business from cyber attacks.
Endpoint Protection / Ransomware Protection
Disaster Recovery
Business Continuity
Data Security and Backup
Where is your data held? If it is held off site for backup purposes, where is it? Who has access to it? Is it encrypted? Knowing where your data is and who has access to it is a major step in ensuring IT security and Cyber Security for your organisation.
Virtual Security Officer
Staff Training
The last line of defense against Cyber attacks is your employees, so training them is essential. The training we provide empowers end users to identify and avert the latest threats within your industry. We offer remote and on-site training for your IT teams and business staff. The training covers cyber security topics, industry trends, and attack vectors tailored to your needs. Annual training is recommended in order to keep your employees up-to-date. Training can also be offered as part of your standard induction process. Recent additions to these courses include topics for distributed work forces, working from home and protecting the corporate assets in this new post-pandemic era.
Free Cyber Security Assessment
Public Discovery Testing
Web Application Scanning
The software first crawls and builds a software construct of the entire website. This gives the scanner an insight into the application, which then performs automatic audit for common security vulnerabilities by launching a series of web attacks. The consultants then manually verify these security vulnerabilities.It would be positioned to check for vulnerability code that has been introduced to the SharePoint Extranets.
Vulnerability Assessment
Penetration Testing
Cyber Security Maturity Assessment
Corporate Risk Management
We assist with the design, build, and run a corporate risk management framework, company security policies, password policies, risk registers and risk assessments – we can come in and hit the ground running for your business to maintain moving forward.
GDPR Readiness
Cyber Essentials and Essentials Plus
Offered as a year round assurance As-A-Service as opposed to annual single audit, we provide an online portal where Cyber Essentials and Plus progress can be tracked easily, quickly and efficiently. With a virtual auditor on hand to assist and carry out the annual assessment this service allows you to keep on top of the accreditation compared to the mad annual panic. A unique addition to this service is our Active Protect agent that will manage, protect and ensure all your devices as Essentials Plus accredited 24x7x365 for a small per device cost – a huge cost saver in terms of technology management and eases the annual assessment by up to 60%. The added benefit of Active Protect allows organisations to distribute their Policies via this lightweight agent and ensure staff read and sign off on them – fully centralised reporting and auditing of these and with this service we also offer FREE Cyber Security Insurance. For more information, visit our Cyber Essentials Information Page
Cyber Resilience-as-a-Service
Managed Security Services
For the best Cyber security protection, Outbound Solutions offer 24/7/365 Managed Security. This is a service consisting of security monitoring, endpoint software, continuous improvement of your environment, and includes constant adjustments to your environment to ensure your business stays safe. Cyber security is an around-the clock exercise. Most organisations cannot maintain an in-house cyber security team, which is why many choose to partner with us, where we give you access to expert security analysts who act as an extension to your internal IT team.
“We’re proud to help our clients thrive!”
– Outbound Solutions Security Team
We offer Cyber Security Assessments that identify potential risks, identify vulnerabilities, and address process improvements to strengthen your security in line with industry standards.
The goal of protecting your business’s data and securing the infrastructure is to establish effective security practices that address critical business requirements.
Performing a cyber security assessment is the best way to identify weak points, manage security risks, and help meet compliance requirements. 65,000+ cyber attacks are committed annually against businesses. Keeping your business secure through cyber security assessments is essential for ensuring basic cyber hygiene, and it provides protection against the catastrophic implications of cyber-attacks. Data breaches can cost SMEs £50-£150k and larger organisations can cost upwards of £500k.
Contact us for a limited Free Cyber Security Assessment
Our tailor-made Cyber Security Assessment is designed to reduce security risks and improve compliance. Our cyber security experts are fully qualified and understand internal and external threats that face businesses.
Would you like an exploratory discussion with an Outbound™ Security Expert?
Build a pathway to technical excellence
No cost and no obligation. Outbound Solutions can help to identify and prevent IT Security and Cyber Security vulnerabilities across your organisation. Our cyber security specialists have helped companies to navigate modern cyber security – now is the time to review your information security risks and improve your cyber security service offerings. Speak to our Cyber Security Team who can provide you with more information.









